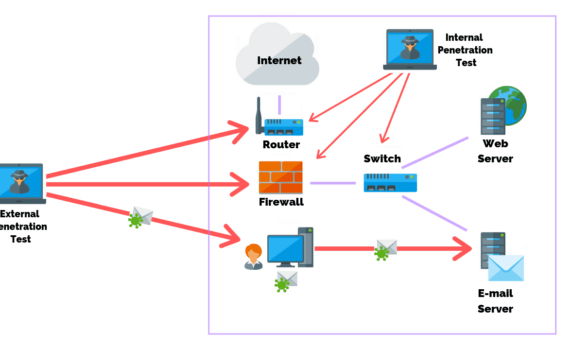
Businesses need to regularly scan the external available infrastructure and applications to protect against external threats. They also need to scan internally to protect against insider threat and compromised individuals. The worst situation is to have an exploitable vulnerability within your infrastructure, application or employees, that you are not aware […]
Daily Archives: January 5, 2020
1 post