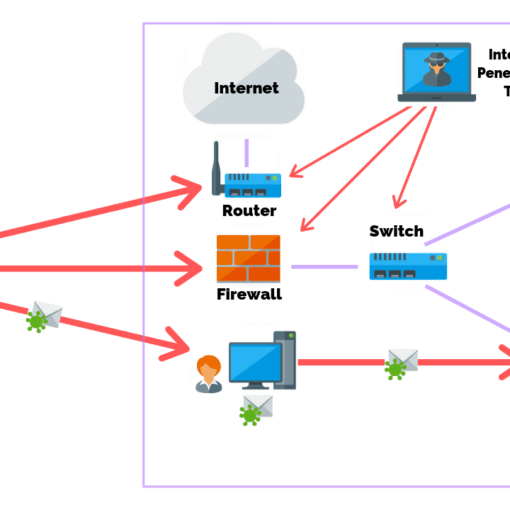
Weak or broken authentication is acknowledged by the OWASP as easily exploitable by hackers with extreme damage potential.
Users need to be authenticated when they are trying to access an application or a service in a reliable, secure (and convenient) manner but this is not always practiced.
81% of data breaches involved weak or stolen credentials.
2017 Verizon Data Breach Investigative Report
Broken Authentication Examples
Broken Authentication may include one or more of the following conditions:
- Permitting weak or well-known, easily discovered passwords
- The lack of multi-factor authentication (MFA) which gives an extra level of security
- Storage of plain-text or weakly-hashed passwords vs. using strong hashes
- Improper invalidation of session when logging out, or after a period of inactivity
- Automated brute-force attacks using known password lists
There are several precautions that can enhance your authentication:
Better passwords
Ensure that users don’t create weak or easily guessed passwords. Set up validation for weak or well-known passwords using a common password list and reject weak passwords.
Encrypt passwords
Ensure all passwords are encypted – hash the user’s password using a strong hashing algorithm (such as Bcrypt or PBKDF2). Never use a weak hash like MD5, and never store your passwords in plain text.
Limit failed logins
Limit the number of consecutive failed login attempts and set a meaningful lockout time, to make it harder for brute force attacks. Some best practices recommended limits on authentication attempts is nine and lockout time 25 minutes.
Limit password lifetime
The longer a password is in use, the more time an attacker has to try to learn it.
Prohibit the reuse of passwords
Force users to select new passwords periodically while checking they are not simply resetting it to the old password or something similar.
Check the quality of new passwords
You can impose a minimum quality standard on passwords
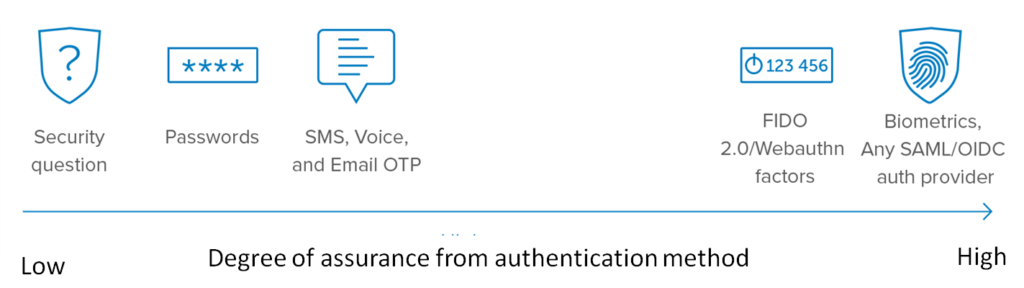
Multi-factor authentication
Multi-factor authentication is an authentication method in which a computer user is granted access only after successfully presenting two or more pieces of evidence to an authentication mechanism: The 3 factors are typically: knowledge (what you know), possession (what you have, like a phone or access to an email account), and biometric (who you are with biometric characteristics like a fingerprint, palmprint, iris, retina etc.)
The usage of multi-factor authentication (MFA) by your application gives an extra level of security because it helps prevent brute force attacks, for example ‘credential stuffing’, as the attacker will not be able to complete the MFA step in a timely, automated way. In addition to a password, MFA enables the use of a mobile device, text message or email or a biometric (like a fingerprint).
Two-factor authentication is a type, or subset, of multi-factor authentication using just two factors, like what you know (password) and what you possess- e.g. passcode received via SMS on your mobile.
Login Failure Messages
When a user enters an incorrect username or password, telling them exactly what they got wrong may make it easier for a hacker to keep trying until they get it right. A good practice is to purposefully use vague login failure messages when users enter an incorrect username or password. The idea is to not let attackers easily identify valid accounts that they could use in an attack.
Conclusion
Authentication approaches continue to improve, but so do the attack capabilities of determined hackers. Even with the best techniques and tools, it is still one of the easiest ways for hackers to break into your network and cause havoc. So be knowledgeable about all the details of how you treat passwords. Be very proactive and implement best practices for password management and introduce multi factor authentication for all your applications.