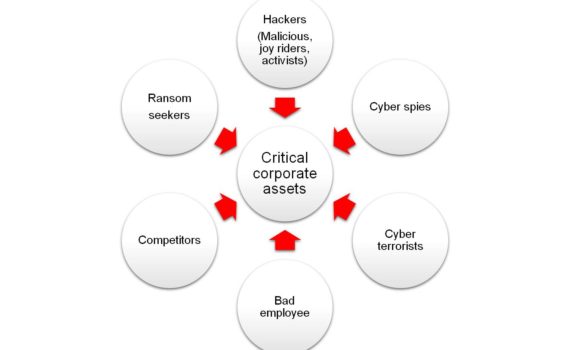
The company board expects the Chief Information Security Officer (CISO) to fulfill several key responsibilities related to cybersecurity and risk management. Here are some common expectations of the CISO: Develop and Implement Cybersecurity Strategy: The board expects the CISO to develop a comprehensive cybersecurity strategy aligned with the organization’s goals […]
Compliance
3 posts
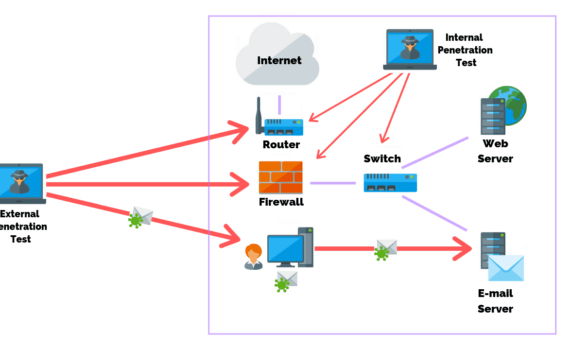
A Hacking Simulation Penetration testing is a hacking simulation conducted with the purpose to create an event as close as possible to a real attack to test an environment’s cybersecurity posture, and eventually identify solutions to secure it, limiting exposure to threats and attacks. Pen-testing is a systematic process that […]
Businesses need to regularly scan the external available infrastructure and applications to protect against external threats. They also need to scan internally to protect against insider threat and compromised individuals. The worst situation is to have an exploitable vulnerability within your infrastructure, application or employees, that you are not aware […]