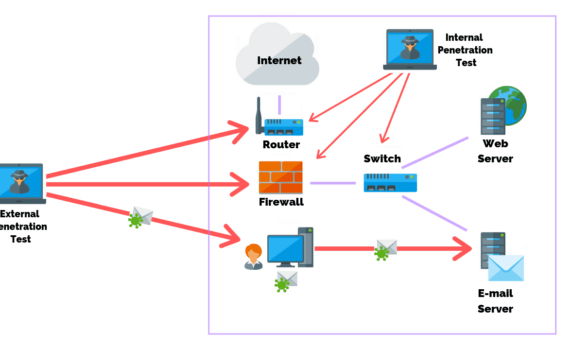
Businesses need to scan the external available infrastructure and applications to protect against external threats. They also need to scan internally to protect against insider threat and compromised individuals. Pen testing should be conducted regularly, from monthly, to possibly quarterly. Because of the constantly evolving threat universe, once a month […]
Penetration tests
3 posts
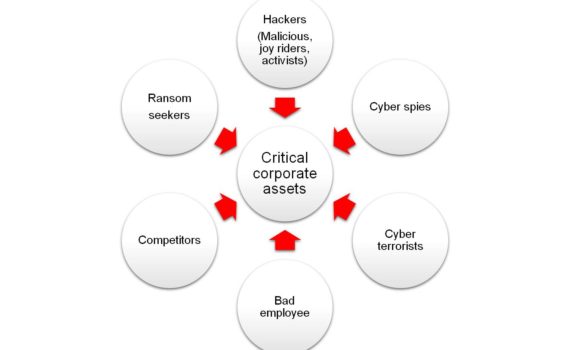
A Hacking Simulation Penetration testing is a hacking simulation conducted with the purpose to create an event as close as possible to a real attack to test an environment’s cybersecurity posture, and eventually identify solutions to secure it, limiting exposure to threats and attacks. Pen-testing is a systematic process that […]
Businesses need to regularly scan the external available infrastructure and applications to protect against external threats. They also need to scan internally to protect against insider threat and compromised individuals. The worst situation is to have an exploitable vulnerability within your infrastructure, application or employees, that you are not aware […]